How to Protect Yourself from Cyber Attacks by Kevin Graham Available from <https://www.quickenloans.com/blog/protect-cyber-attacks> [ December 7, 2016]
Remember last month when hackers were briefly able to disrupt service to popular websites such as Netflix, Twitter, Spotify and Etsy for several hours? Whatever their motivations, there’s no doubt the hackers had a plan and were skilled. Still, even when something happens that affects large portions of the internet, there are things we can learn to help protect ourselves as individuals now and in the future.
As we enter a time of year when everyone’s going to be doing a lot of online shopping, we thought we would give you some tips to help you keep your information secure. Let’s start by going over exactly what happened last month and what we can learn from it.
Anatomy of an Internet Takedown
So what exactly took down so many websites last month? It was something called a distributed denial of service (DDoS) attack. The attackers picked a major internet hosting service on the East Coast and sent a bunch of traffic to the sites it hosted – so much that it overloaded the servers.
The first job of any internet server is to take your request (to go to, say, QuickenLoans.com) and translate that into a request the computer can understand. You type in your web address, and the computer turns what you typed into a series of numbers called an internet protocol (IP) address. In your web browser, when you enter QuickenLoans.com, the server goes and looks up the IP address associated with that domain, maybe 10.168.64.9, and gets you to the right place. It’s like a giant phonebook, except we don’t throw it out as soon as it arrives.
Normally, all this traffic gets routed, and everything goes smoothly. When a server gets thousands of requests to go to a particular website, though, it creates a traffic jam. The server is overloaded, and the site is unreachable until the host is able to identify the attack and take mitigating measures. But what measures did they take?
We have a thousand devices connected to the internet these days. It’s not just computers, but also DVRs, webcams and even our thermostats. The attackers were able to get into these newly internet-enabled devices and use them to send a bunch of traffic to sites and overload the servers. I don’t mean to say that the webcam in the nursery was sending a request to Netflix to watch “Zootopia.” This was unsophisticated nonsense traffic – uploads and downloads meant purely to flood the servers. There’s been lots of really good, detailed analyses of what happened in the attack, but what’s more helpful for those of us trying to protect ourselves is knowing exactly how they did it.
Tyranny of the Default
So what was the weak point in all of these devices that allowed them to be so easily taken over? No one ever changed the password.
Most of these internet-connected appliances have a default password listed in the manual so you can easily get them set up. Unfortunately, many people never think to change the password. If you find yourself in this situation, follow your device’s instructions to get back into the settings and change the password if possible.
In some instances, depending on the sophistication (or lack thereof) of a particular device, there may not be a way to change the default. In these instances, manufacturers will sometimes send updates that patch the software and help to secure the device. Always run these updates, particularly if they mention anything about fixing bugs or improving security.
As we enter the holiday season and you’re looking at getting that new flat-screen TV on Cyber Monday, make sure you’re using strong passwords. You can even get online password generators like LastPass or 1Password that will enable you to have one password that unlocks all your accounts but still maintains the security of having many different passwords.
Secure Your Wi-Fi
Securing your internet connection is key if you want to keep your internet browsing to yourself. Without a secured connection, hackers have the opportunity to get on the network and put themselves between you and your hotspot or router. Instead of going directly to your connection point, your data goes through the hacker first, and they get a peek at what you’re doing before your data goes on to its ultimate destination. Depending on how your sharing settings are configured, a nefarious actor may also be able to get malware onto your computer.
The level of encryption used can be changed, and it’s up to you. At the very least, your router should be password-protected.
Security in Public
The other thing you should know is how to take steps to secure yourself in public. When you need to check your bank account, sometimes the only available connection is the coffee shop.
When you find yourself in these situations, the most important thing to remember is that websites asking for sensitive information should be secured and encrypting your data as it’s passed through. While someone with malicious intent might still be able to see your activity, usernames, passwords and credit card numbers, it usually ends up looking like unintelligible gobbledygook unless it can be decrypted. Most hackers don’t want to take the time and effort to do this.
How do you know if you’re on a secure site? In the address bar, you should see a green HTTPS mark at the beginning of the web address. If you choose, you can also click on this mark to see who owns the security certificate and make sure you’re giving your information to the right people.
It’s always a good idea to check for the secured symbol whenever you’re putting in sensitive information like credit card numbers. Here’s what it looks like:
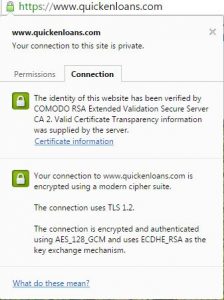
You should also make sure that any time you log into a public connection, you select the public option when you connect. Your operating system will put certain security protocols in place that you might not need for a home network – just to give you a little more protection. A lot of the settings have to do with your ability to share files on the network.
Device and App Permissions
While we’re on security, it’s a good time to talk about the smart phones that now hold the keys to so much of our lives. Your phone is equal parts Rolodex, wallet, health information repository and camera. If the wrong person were to get ahold of all that, it could cause you a serious headache.
With that in mind, you should take some reasonable precautions to protect your phone from prying eyes.
First, make sure you set a passcode on your phone. Not only will this prevent your little sister from getting into your phone, but on newer iPhones, setting a passcode automatically encrypts the data against anyone who doesn’t have your code or fingerprint. By default, this is a four-digit numerical password, but you have the option to switch to a longer alphanumeric key.
Since device manufacturers have much more control over the look of the Android interface, the name of your encryption setting may vary. That said, it should be with your security settings. If encryption isn’t enabled by default on your device, there are some things you should be aware of before going through with the process.
Be sure you know the permission you’re giving apps when you use them. If you’re on iOS or newer versions of Android, your phone will ask you permission before accessing something like your photos, camera or contacts. It can be tempting to answer yes to everything so the app stops bugging you. I’ve been guilty of this, too. If you’ve ever given an app access to something and later regretted it, there are ways to reverse it.
If you go into your iPhone’s privacy settings, you can control which apps have access to your location, your media library, and your health and fitness data, among other items. Android versions Marshmallow and up include the option to control the permissions under the apps tab of your settings.
In older versions of Android, the permissions were listed when you went to install the app. Unfortunately, you don’t have control over individual permissions by default.
Finally, one special note regarding Android: In addition to installing apps from the Google Play Store, you have the option of installing apps from third parties. This is OK if you know what you’re doing, but if you’re not careful, it opens your phone up to malware. You can disable this option in your security settings.
Depending on the types of things you do on your phone, you might want to limit what gets backed up to the internet and keep local control on your phone. There’s always a bit of a push-pull relationship between security and convenience. You have to decide what works for you.
These basic security measures are important because they can help you avoid the hassle and inconvenience associated with identity theft.
How to Protect Yourself from Cyber Attacks by Kevin Graham Available from <https://www.quickenloans.com/blog/protect-cyber-attacks> [ December 7, 2016]






